Exploring SSO Solutions in Azure AD B2C
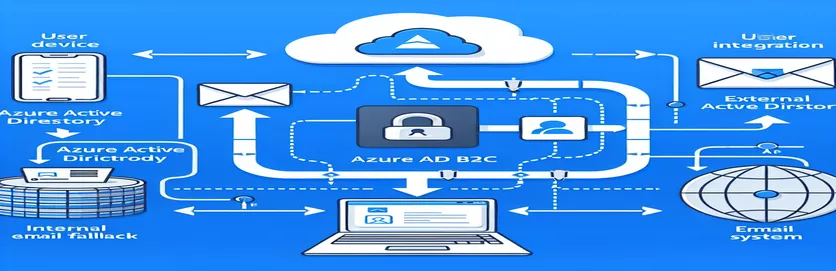
Single Sign-On (SSO) is a key technology in the field of digital identity management that allows users to log into various apps with just one set of login credentials. This ease of use is particularly important in settings that use Azure Active Directory B2C, or Azure AD B2C, as a smooth user experience may greatly improve security and user happiness. A sophisticated method of identity management is represented by the integration of SSO using an external Active Directory (AD) email address, with a fallback to an internal B2C email account. It offers a strong framework for managing identities across many platforms in addition to streamlining the authentication process.
A detailed grasp of both Azure's identity services and the external AD's settings is necessary for implementing SSO in Azure AD B2C with an emphasis on leveraging email addresses from the external AD. This configuration guarantees a smooth transition to apps managed by Azure AD B2C for users who work primarily in the external AD environment. An essential feature that guarantees users who lack an external AD account or have trouble accessing it may still authenticate with ease is the fallback to an internal B2C email address. By supporting a variety of user scenarios, this dual strategy improves the adaptability and usability of apps inside the Azure environment.
| Command | Description |
|---|---|
| B2C Custom Policies for Azure AD | Outlines the user paths inside your Azure AD B2C directory, enabling intricate authentication processes that incorporate third-party identity suppliers. |
| Identity Experience Framework | A collection of Azure AD B2C features that let programmers alter and expand how the authorization and authentication procedures behave. |
| Azure AD External Identities | Sets up Azure AD to accept sign-ins from users in external identity providers, including social media accounts or other Azure AD organizations. |
Examining SSO Integration in-depth with Azure AD B2C
SSO can be integrated with an external Active Directory (AD) and Azure Active Directory B2C (Azure AD B2C) to provide a simplified authentication procedure that improves security and user experience. By enabling users to log in using their external AD email addresses, this connection eliminates the need for multiple logins and provides for a smooth transition between services. This solution is significant because it makes use of pre-existing corporate credentials, which lessens the cognitive burden on users and lowers the dangers involved in managing numerous sets of credentials. Furthermore, by centralizing user authentication and strengthening control over user access and behavior, it complies with security best practices.
An essential component of this configuration is the fallback mechanism to an internal B2C email address, which guarantees that access is maintained for users who do not have an external AD account or who experience problems with their external AD login. In addition to optimizing accessibility, this dual-strategy guarantees that businesses can serve a wide range of users, such as independent freelancers, contract workers, and outside partners who might not be a part of the external AD. The Azure AD B2C environment must be carefully planned and configured in order to implement such a system. This includes setting up unique policies and technical profiles that specify how authentication requests are handled and how fallback mechanisms are activated in the event that primary authentication methods fail.
Configuring Azure AD B2C to Use an External AD Backup
Azure Portal Configuration
<TrustFrameworkPolicy xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"xsi:noNamespaceSchemaLocation="http://azure.com/schemas/2017/03/identityFrameworkPolicy.xsd"><BasePolicy><TenantId>yourtenant.onmicrosoft.com</TenantId><PolicyId>B2C_1A_ExternalADFallback</PolicyId><DisplayName>External AD with B2C Email Fallback</DisplayName><Description>Use External AD and fallback to B2C email if needed.</Description></BasePolicy></TrustFrameworkPolicy>
Setting Up Azure AD B2C External Identity Providers
Configuring Identity Framework XML
<ClaimsProvider><Domain>ExternalAD</Domain><DisplayName>External Active Directory</DisplayName><TechnicalProfiles><TechnicalProfile Id="ExternalAD-OpenIdConnect"><DisplayName>External AD</DisplayName><Protocol Name="OpenIdConnect" /><Metadata><Item Key="client_id">your_external_ad_client_id</Item><Item Key="IdTokenAudience">your_audience</Item></Metadata></TechnicalProfile></TechnicalProfiles></ClaimsProvider>
Examine Azure AD B2C SSO in-depth using internal and external email strategies.
A sophisticated approach to identity management is represented by the implementation of Single Sign-On (SSO) in Azure Active Directory B2C (Azure AD B2C) utilizing an external Active Directory (AD) email address, supplemented by a fallback to an internal B2C email address. This approach meets the needs of companies that want to simplify access between different internal and external platforms, all the while improving user experience and upholding strict security protocols. This setup's main benefit is its flexibility in terms of authentication methods, which enables customers to engage with Azure AD B2C applications without requiring additional identities or credentials, even from external AD environments. By combining them under Azure AD B2C, it solves the common issue of managing several identity stores and streamlines the user authentication process.
When external AD authentication fails—either because of technical difficulties or because the user lacks an external AD account—the fallback mechanism to an internal B2C email address is especially helpful. By doing this, the user experience is maintained and access to applications is guaranteed. Furthermore, by utilizing this configuration, enterprises can take use of Azure AD B2C's strong security features, such multi-factor authentication and conditional access controls, for all user accounts—regardless of whether they are native to Azure AD B2C or originate from an external AD. Careful planning and configuration are necessary for the implementation of such a comprehensive SSO solution, including the integration of external identity providers and the creation of custom policies in Azure AD B2C.
Frequently Asked Questions Concerning the Integration of Azure AD B2C SSO
- What is B2C Azure AD?
- Microsoft's customer identity and access management solution, Azure Active Directory B2C, is made to accommodate several authentication techniques for both internal and external apps.
- How does Azure AD B2C SSO work?
- Azure AD B2C facilitates SSO by allowing users to configure identity providers and custom policies, allowing users to log in once and access different applications without re-authenticating.
- Can external ADs be integrated with Azure AD B2C?
- Yes, Azure AD B2C can interface with external ADs, allowing businesses to access B2C apps using their current AD login credentials.
- What Azure AD B2C SSO fallback mechanism is there?
- In the event that the external AD authentication fails or is unavailable, the fallback method entails authenticating using an internal B2C email address.
- How can SSO be set up in Azure AD B2C?
- Setting up identity providers in the Azure AD B2C portal, creating custom policies, and incorporating these policies into your applications are all part of configuring SSO.
- Is multi-factor authentication compatible with Azure AD B2C SSO?
- Sure, multi-factor authentication is supported by Azure AD B2C. By demanding extra verification, this increases the security of single sign-on.
- How is user data privacy handled by Azure AD B2C?
- Azure AD B2C is built with privacy in mind, protecting user data by adhering to international norms and laws.
- Is it possible to personalize the Azure AD B2C user journey?
- Yes, the user journey and authentication flows may be deeply customized using Azure AD B2C's Identity Experience Framework.
- How do users of external ADs get access to B2C apps?
- Because Azure AD B2C integrates with external AD, users of external AD can access B2C applications through SSO by logging in with their AD credentials.
Conclusions Regarding the Integration of External AD with Azure AD B2C
SSO implementation in Azure AD B2C with an external AD email address and an internal B2C email fallback option is a big step toward making access control easier for businesses. By eliminating the need for numerous logins, this method not only improves user experience but also makes use of Azure AD B2C's strong security features. The solution is inclusive without sacrificing security thanks to its adaptability to users from various identity providers. Additionally, the fallback approach ensures that access will always be possible, even in the event that external AD authentication fails. The significance of these integrated authentication systems grows as companies continue to extend their online presence. This method is a crucial part of contemporary identity management techniques since it simplifies the authentication process and complies with user expectations about security and privacy.